ABSTRACT
Cyber risks are one of the most substantial risks resulting from the development of technology. Since traditional policies are not sufficient to cover risks deriving from cyber risks, insurance companies have begun producing and selling cyber insurance policies. Generally, cyber insurance policies include both third-party and first-party damages, but they could be specialized since every sector and enterprise has different risks. Because cyber insurance policies are a new issue in the insurance sector, there is a big gap. This article will focus on the necessity of cyber risk insurance, differences between traditional policies, specialization of the policies, and lastly solutions to the problems.
KEYWORDS: Cyber Risk, Cyber Insurance Policy, Insured, Insurer and Cyber Attack
I-INTRODUCTION
Cybersecurity is a very vital subject in today’s world. It is because of the developing technology and the sophistication of hackers. Therefore, Cyber risks could be cited as one of the most dangerous risks of the twenty-first century. Many types of businesses such as retail stores, healthcare entities, and financial institutions, as well as government entities, could be subject to cyber-attacks.[1] Every reported data breach or system failure incident could result in high financial or reputational losses.[2] This will cause great problems in companies, non-governmental organizations, governments and etc. For example, in 2016 a distributed denial of service (DDoS) attack gave rise to an interruption on the internet connection of millions of people for a few hours, causing big losses.[3] In a different example, intelligence agencies in the United States accused the Russian Government by virtue of interference of the election process in the USA.[4] Relevant events have been realized through cyber attacks. As it will be explained below, cyber-attacks may occur in different ways. The most common ones of cyber attacks are denials of service, ransomware, phishing scams, and computer hacks.[5] New types of cyber attacks are also emerging day by day.
Relevant cyber attacks have several potential negative consequences, intellectual property rights of third and first parties could be stolen, customers’ confidential information also could be stolen, IT (Information Technology) systems of the companies or institutions could be broken, and financial losses could occur in the companies and reputation of the institutions or companies may be damaged.[6] Economic damages to companies or other entities are incredible; it is predicted that by 2025 damages arising from cyber attacks will reach to $10.5 trillion.[7] The aforementioned damages will not be limited to financial losses. Therefore, creating an insurance system for cyber risks is very important, because traditional insurance policies may not be sufficient to meet the needs for cyber risks. With this article legal perspective of cyber risk, insurance will be explained.
In this article, firstly, the conception of cyber risk, secondly, types of cyber risks, thirdly types of insurable cyber risks and exceptions, fourth, issues to be considered in the course of the preparation process of the cyber insurance agreement, fifthly, cyber risk insurance in Turkey and TCC (Turkish Commercial Code) and lastly problems and potential solutions within the scope of conclusion will be explained and described.
II-CONCEPTION OF CYBER RISK
The invention of the internet led to the emergence of many new technologies. Afterward, the widespread usage of relevant information technologies gave rise to new threats.[8] Companies are in a transformation process regardless of their size.[9] Since the usage of information technology is increasing day by day, threats that companies face are also increasing. One of the most important risks arising from this development is cyber risk. For instance, six Russian nationals were accused to be officers in Russia’s service and they were indicted by the U.S. Department of Justice for their roles in cyber-attacks that were committed against Ukraine, Georgia, France, South Korea, and the United States.[10]
Basically, the term cyber-risk could be defined as risks that affect and damage information and technological assets of the film arising from different sources.[11] There are several different opinions when defining cyber risk. Some scholars express that cyber-risk is a malicious electronic event that leads to disruption of business and monetary loss; other scholars say that it is a failure occurring in the information systems which is broader.[12] The National Research Council (NRC) described cyberattacks as “the use of deliberate actions—perhaps over an extended period of time—to alter, disrupt, deceive, degrade, or destroy adversary computer systems or networks or the information and/or programs resident in or transiting these systems or networks.”[13] Cyber risks affect different organizations such as government agencies, universities, financial sectors and generally all industries, emergency services, healthcare and etc.[14] Since cyber-attacks can be committed from thousands of miles away, normal precautions are not sufficient for them, therefore they are too different in terms of location and visibility.[15] In order to determine an entity’s potential for cyber-risk losses, it is important to detect what type of business relevant entity is engaged in.[16] Types of cyber-attacks could be exemplified as malware, phishing and social engineering, web-based attacks, malicious code, botnets, stolen devices, Denial of service (DoS) and malicious insiders according to 2016 dated The Ponemon Institute Report.[17] In the next chapter detailed version of types of cyber crime will be explained.
III-TYPES OF CYBER RISKS
Cyber risk may arise from both natural (earthquake, flood, fire and etc.) and human based events.[18] Human based cyber risks could be exemplified as malware, phishing and social engineering, web based attacks, malicious code, botnets, stolen devices, Denial of service (DoS) and malicious insiders as explained above. If it is necesarry to explain human based risks, they are mostly cyber attacks. For example; ransomware could be defined as a form of malware which is created to encrypt files on targeted device, by virtue of this, it makes the system unusable.[19] In addition to this, a DDoS (Distributed Denial of Service) attack could be defined as an attack in which targeted server is exposed overwhelming request and relevant requests makes the system unusable.[20] Also, phishing could be defined as “A technique for attempting to acquire sensitive data, such as bank account numbers, through a fraudulent solicitation in email or on a web site, in which the perpetrator masquerades as a legitimate business or reputable person.”[21] Human based cyber risks are not limited with these examples and with the development of the technology, number of human based cyber risks are increasing. Even if human based cyber risks are mostly related to data infringement, different losses could occur such as intellectual property theft.[22]
As there are types of risks, there are also types of losses arising from cyber risks. Losses arising from cyber risk could be in different types. Mostly, two types of losses are accepted by scholars. First party losses could be defined as losses that are profits and expenses due to property damage (lost data, software, hardware) and business interruption cost resulting from cyber risks.[23] Third party losses are losses which are incurred over third parties either directly or indirectly due to cyber attacks.[24]
Conception of cyber risks and types of cyber risks have been explained above. As explained in introduction part since cyber risks lead to huge damages on companies and other institutions, insurance of cyber risk is very important. Therefore, insurance of cyber risks will be described in the next part of the article.
IV-INSURANCE OF CYBER RISKS
Pursuant to scholars, cyber insurance is a broad term which is used for special policies insuring covering first and third party losses arising from cyber attack or failure in information technology system of company.[25] As known that traditional insurance policies is not sufficient to cover losses for non-physical property damage and electronic data; therefore, traditional insurance policies have many gaps in coverage for cyber risks.[26] The most substantial gap in traditional policies is that there is no “trigger” provision that could create protection for an insured in the event of a data breach; also, losses with respect to unauthorized access to protected consumer information may not be covered in traditional insurance policies.[27] Furthermore, mostly geographical limitations could be a big problem for cyber risks and finally, since insurer companies began designating new cyber-risk specific insurance products, they refuse to cover cyber risks based on traditional policies.[28]
A-Insurable Cyber Risks
As explained above, cyber risk policies provide coverage for both first party and third party losses. In the table[29] below, comparison with respect to first party and third party losses/risks will be given.
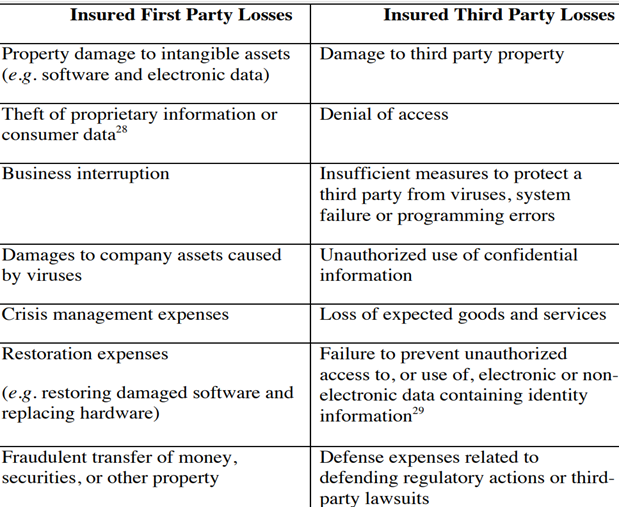
(Table 1: First Party and Third Party Losses/Risks)
1-First Party Losses/Risks
First Party Losses/Risks are losses wich directly affect insured organization due to cyber risk.[30] In other words, these risks/losses directly belong to the insured company. Categories of first party losses/risks could be exemplified as damages occuring over intangible assets such as software and electronic data, bussiness interruption, the theft of proprietary information or consumer data, viruses, extortion, programming errors and other system or network failure.[31]
2-Third Party Losses/Risks
In cases where third party losses/risks are guaranteed in the cyber risk policy, relevant policy guarantees obligation of insured party against third parties.[32] Categories of third party party losses/risks could be exemplified as company’s liability for damage to third party property consisting of intangible assets, namely software (programs) and data and or financial losses as a result of: denial of access, insufficient measures used to protect third-party from computer crime, spread of a computer virus, failure of software, and programming errors any or all of which lead to network or system failures or loss of expected goods and services, harm to digital assets, defamation and privacy breaches and where the insured party has a contractual duty to indemnify any third party.[33]
B-Exceptions
As known, damages which could occur due to cyber risks are unpredictable. Therefore, if insurer companies do not write their reservations in the policies, they could face very bad consequences. Because of this reason there are several exceptions which are commonly included in cyber insurance policies. For example: unless accepted otherwise, foreign activities of insured company, competition, restriction of commerce and taxation, self-inflicted losses, accessing unsecured websites, espionage and terrorism, bodily injury and property damages using copy software, consultancy getting by insured companies, damages arising from pollution, and loss of datas from non-encrypted devices are mostly excluded from cyber insurance policies.[34]
As a result, scope of cyber insurance policies has been explained in this part of the article. In the next part issues to be considered in the course of preparation process of the cyber insurance policies will be taken into consideration.
V-ISSUES TO BE CONSIDERED IN THE COURSE OF PREPARATION PROCESS OF THE CYBER INSURANCE POLICIES
Concerns in the course of prepaprepration of cyber insurance policies are different for both insurer and insured (policyholder). Both issues are going to be evaluated below.
A-For the Insurer
It is very important for the insurer company to detect the risks of the insured in the course of preparing cyber insurance policies; therefore, questions to be asked to the insured companyhave significant importance.[35] For the questions to be asked to the insured, article 1436 of the Turkish Commercial Code (TCC) numbered 6102states that “(1) If the insurer has given to the policyholder (insured) a list of questions to be answered, the policyholder (insured) shall not be liable for any circumstances remaining outside the scope of the questions contained in that list unless the policyholder (insured) has hidden an important issue in bad faith. (2) The insurer may also ask questions about circumstances not in the list . These questions have to be in writing and clear. The policyholder (insured) has to answer these questions.”
Therefore, in accordance with article 1436 of TCC, the insurer must ask the necesary questions to the insured company regarding organization of the insured company, technical infrastructure of the insured company and policy and produres of the insured company; otherwise, the insured company does not have any reponsibility arising from the problems which are not asked by insurer.[36]
B-For the Insured(Policyholder)
When any company or individual wants to sign cyber insurance policy with any of insurercompany, there are several issues which have to be taken into consideration. First of all they have to examine different types of products of the insurer company and they have to decide which of relevant products are suitable for their company; secondly, the candidate company must ask to the insurer company that whether they have specialized products for cyber risk or not, because it is important in cyber insurance policies; thirdly, they could also determine retroactive date because mostly it could be difficult to detect scope of data infringements; forthly, it is also important to examine the conditions, guarantees and definitions in cyber insurance policies and lastly, prerequisites which are determined in the policy could also be important since in case insured company does not meet relevant conditions, it could not benefit form the policy.[37] Relevant issues must be taken into consideration by insured companies or individuals, otherwise they could deal with serious problems.
In this part of the article concerns in the course of preperation of cyber insurance policies has been examined in terms of both insurer and insured. In the next part of the article cyber risk policies in accordance with TCC will be described.
VI-CYBER RISK INSURANCE IN ACCORDANCE WITH TCC(TURKISH COMMERCIAL CODE)
Pursuant to Turkish Law, provisions of the sixth book of the Turkish Commercial Code numbered 6102 regarding insurance law will be applied to cyber insurance policies. Since cyber risk insurance policy could include both liability and property insurance, in addition to general provisions, provisions regarding liability and property insurance could be applied in cyber risk insurance policies.[38] Since cyber risk insurance policies are new in Turkey, there is no common application of these policies.
VII-CONCLUSION
With the development of technology and communication, companies and individuals are obliged to face new risks. As explained above, cyber risks are one of the most important risks arising from technology in today’s world. Potential damages which could occur with respect to cyber risks are unpredictable. By virtue of this, companies and individuals could have to face huge damages. However, there are several precautions that companies and individuals could take in order to minimize the risks regarding cyber risks. Insurance of cyber risks is one of the most substantial ones of these precautions. Traditional policies are not sufficient to cover the risks arising from cyber risks because as explained above the most substantial gap in traditional policies is that there is no “trigger” provision that could create protection for an insured in the event of a data breach; also, losses with respect to unauthorized access to protected consumer information may not be covered in traditional insurance policies. In addition to this, since every sector has different risks, specialization is necessary in cyber insurance policies. Also, a cyber risk insurance policy could include both liability and property insurance, regulations in effect today are not sufficient. Furthermore, in Turkey, most of companies do not have information regarding cyber insurance policies. As a result, the first thing that needs to be done is to raise awareness regarding cyber risks and the consequences of these risks. Secondly, since regulations in effect are not enough to include cyber risks, revising TCC in accordance with cyber risk insurance or enacting a new code that is directly related to cyber risk insurance is needed. Otherwise, companies or individuals may face serious consequences.
BIBLIOGRAPHY
- Karayazgan A. , Hukuki Yönüyle Siber Riskin Sigorta ve Reasüransı(1st edn. Legal Yayıncılık 2020)
- French C.C, “Five Approaches to Insuring Cyber Risks”(2021), 81 Md. L. Rev. 103 (2021), < https://papers.ssrn.com/sol3/papers.cfm?abstract_id=3811826 >, accessed at 31.05.2022.
- Biener C., Eling M. and Wirfs J. H. , “Insurability of Cyber Risk: An Empirical Analaysis”(2015), Geneva Papers on Risk and Insurance, Vol. 40, No. 1, 2015, < https://papers.ssrn.com/sol3/papers.cfm?abstract_id=2577286 > , accessed at 31.05.2022.
- Kesan J. P. and Hayes C. M., “Strengthening Cybersecurity with Cyberinsurance Markets and Better Risk Assessment”(2017), 102 Minn. L. Rev. 191 (2017), <https://papers.ssrn.com/sol3/papers.cfm?abstract_id=2924854 >, accessed at 31.05.2022.
- Shackelford S. J., “Wargames: Analyzıng the Act of War Exclusıon in Cyber Risk Insurance Coverage and its Implicatıons for Cybersecurity Policy”(2020), , YALE JOURNAL OF LAW AND TECHNOLOGY (Forthcoming 2021), < https://papers.ssrn.com/sol3/papers.cfm?abstract_id=3746754 >, accessed at 01.06.2022.
- Petersa G. V. , Pavel V.. Cohenc S. R. D. and Mauriced D. , “Understanding Cyber Risk and Cyber Insurance”(2018) , Macquarie University Faculty of Business & Economics Research Paper, < https://papers.ssrn.com/sol3/papers.cfm?abstract_id=3200166 >, accessed at 01.06.2022.
- Bailey L. M. D. , “Mitigating Moral Hazard in Cyber-Risk Insurance”(2014), 3 J.L. & CYBER WARFARE 1 (2014), < https://papers.ssrn.com/sol3/papers.cfm?abstract_id=2424958 >, accessed at 01.06.2022.
- Atuntaş E. , Kara E., Soylu A. B. and Kırkbeşoğlu E., “Siber Sigortalar: Son Gelişmeler, Uygulamalar ve Sorunlar”(2018), Bankacılık ve Sigortacılık Araştırmaları Dergisi, Sayı: 12, Aralık 2018, < https://dergipark.org.tr/tr/download/article-file/610968 >, accessed at 02.06.2022.
- Rawlings P. , “Cyber Risk: Insuring the Digital Age”(2015), British Insurance Law Association Journal, 2015, volume 128, < https://papers.ssrn.com/sol3/papers.cfm?abstract_id=2551421 >, accessed at 02.06.2022.
- The National Research Council (NRC) Report, note 29, at 80.
- https://cybersecurityventures.com/hackerpocalypse-cybercrime-report-2016/ , accessed at 31.05.2022.
- https://www.ponemon.org/local/upload/file/2016%20HPE%20CCC%20GLOBAL%20REPORT%20FINAL%203.pdf, accessed at 01.06.2022.
- https://www.bgasecurity.com/2021/11/ransomware-saldirilarini-nasil-tespit-edebilirsiniz/ , accessed at 01.06.2022.
- https://usa.kaspersky.com/resource-center/threats/ddos-attacks accessed at 01.06.2022.
- https://csrc.nist.gov/glossary/term/phishing accessed at 01.06.2022.
*Istanbul Medeniyet University, Institute of Post Gradute Studies, Private Law Student.
[1] Christopher C. French, “Five Approaches to Insuring Cyber Risks”(2021), 81 Md. L. Rev. 103 (2021), < https://papers.ssrn.com/sol3/papers.cfm?abstract_id=3811826 >, 105, accessed at 31.05.2022.
[2] Christian Biener, Martin Eling and Jan Hendrik Wirfs, “Insurability of Cyber Risk: An Empirical Analaysis”(2015), Geneva Papers on Risk and Insurance, Vol. 40, No. 1, 2015, < https://papers.ssrn.com/sol3/papers.cfm?abstract_id=2577286 > , 1, accessed at 31.05.2022.
[3] Jay P. Kesan and Carol M. Hayes, “Strengthening Cybersecurity with Cyberinsurance Markets and Better Risk Assessment”(2017), 102 Minn. L. Rev. 191 (2017), <https://papers.ssrn.com/sol3/papers.cfm?abstract_id=2924854 >, 192, accessed at 31.05.2022.
[4] Kesan and Hayes(n.3)192.
[5] French(n.1)105.
[6] French(n.1)105
[7] Available at https://cybersecurityventures.com/hackerpocalypse-cybercrime-report-2016/ , accessed at 31.05.2022
[8] Ahmet Karayazgan, Hukuki Yönüyle Siber Riskin Sigorta ve Reasüransı(1st edn. Legal Yayıncılık 2020)3.
[9] Karayazgan(n.8)3.
[10] Scott J. Shackelford, “Wargames: Analyzıng the Act of War Exclusıon in Cyber Risk Insurance Coverage and its Implicatıons for Cybersecurity Policy”(2020), , YALE JOURNAL OF LAW AND TECHNOLOGY (Forthcoming 2021), < https://papers.ssrn.com/sol3/papers.cfm?abstract_id=3746754 >, 4, accessed at 01.06.2022.
[11] Biener, Eling and Wirfs(n.2)2.
[12] Biener, Eling and Wirfs(n.2)3.
[13] Kesan and Hayes(n.3); The National Research Council (NRC) Report, note 29, at 80.
[14] Gareth W. Petersa, Pavel V. Shevchenkob, Ruben D. Cohenc and Diane Mauriced, “Understanding Cyber Risk and Cyber Insurance”(2018) , Macquarie University Faculty of Business & Economics Research Paper, < https://papers.ssrn.com/sol3/papers.cfm?abstract_id=3200166 >, 3, accessed at 01.06.2022.
[15] Liam M. D. Bailey, “Mitigating Moral Hazard in Cyber-Risk Insurance”(2014), 3 J.L. & CYBER WARFARE 1 (2014), < https://papers.ssrn.com/sol3/papers.cfm?abstract_id=2424958 >, 5, accessed at 01.06.2022.
[16] Bailey(n.15)5-6.
[17]Available at https://www.ponemon.org/local/upload/file/2016%20HPE%20CCC%20GLOBAL%20REPORT%20FINAL%203.pdf, accessed at 01.06.2022.
[18] Karayazgan(n.8)8.
[19] Available at https://www.bgasecurity.com/2021/11/ransomware-saldirilarini-nasil-tespit-edebilirsiniz/ , accessed at 01.06.2022.
[20] Available at https://usa.kaspersky.com/resource-center/threats/ddos-attacks accessed at 01.06.2022.
[21] Available at https://csrc.nist.gov/glossary/term/phishing accessed at 01.06.2022.
[22] Karayazgan(n.8)8.
[23] Bailey(n.15)7.
[24] Bailey(n.15)7.
[25] Karayazgan(n.8)28.
[26] Bailey(n.15)8.
[27] Bailey(n.15)8.
[28] Bailey(n.15)8.
[29] Bailey(n.15)9.
[30] Eda Atuntaş, Emine Kara, Abdullah Buğra Soylu and Erdem Kırkbeşoğlu, “Siber Sigortalar: Son Gelişmeler, Uygulamalar ve Sorunlar”(2018), Bankacılık ve Sigortacılık Araştırmaları Dergisi, Sayı: 12, Aralık 2018, < https://dergipark.org.tr/tr/download/article-file/610968 >, 13, accessed at 02.06.2022.
[31] Bailey(n.15)9.
[32] Altuntaş, Kara, Soylu and Kırkbeşoğlu(n.30.)13.
[33] Bailey(n.15)8-9; Philip Rawlings, “Cyber Risk: Insuring the Digital Age”(2015), British Insurance Law Association Journal, 2015, volume 128, < https://papers.ssrn.com/sol3/papers.cfm?abstract_id=2551421 >, 11, accessed at 02.06.2022.
[34] Karayazgan(n.8)51-57.
[35] Karayazgan(n.8)61.
[36] Karayazgan(n.8)61-64.
[37] Karayazgan(n.8)64-68.
[38] Karayazgan(n.8)41.

